By: Scott Busby, Security Engineer, MAD Security | February 1, 2019
The name ransomware comes from a not particularly clever combination of the words “ransom” and “malware”. First seen in 2013, ransomware is a type of evolving malware that attempts to encrypt files on a target system and make them unusable for the victim. The attacker then informs the victim that for a hefty fee (often paid in Bitcoin) they can regain access to their data. Losing access to data can be a showstopper for businesses, and for individuals with important photos or documents; it can also be emotionally devastating.
Victims essentially only have three options for getting their data back. The first and most obvious option is to just pay the ransom. Not only is this option costly, but you have no guarantee that the attacker will actually decrypt your data after receiving payment. The second option is to discover the private key that the attacker used to encrypt your data. In most instances this isn’t really an option, however there have been some cases of attackers hardcoding decryption keys that have been documented, but for the most part, brute forcing the private key used to decrypt the data would require nation-state level resources and a long-time commitment. The third and best option (if available) is to just simply restore the data from a backup. In this scenario, having a backup could save your company hundreds of thousands of dollars and reinforces just how critical backing up data is!
Although ransomware attacks have trended downward significantly since their 2013 debut, as much as 16,000 ransomware related threats were reported every day in Q2 of 2018. Ransomware is profitable for attackers and is unlikely to go away anytime soon. In the sections below, I will explain characteristics of ransomware as well as some practical defenses against it.
Ransomware Biology
In this post we have randomly selected a notPetya ransomware sample from VirusTotal. VirusTotal is a website used to upload and scan files for malicious code. Reviewing the characteristics of a random ransomware sample will provide the most context to the complexities and nature of this malware. One of the more complicating parts of this sample review is understanding that each sample could have small or major differences making its digital signature different from the next, but this will give a basic understanding of how a ransomware strain may operate.
Review of a VirusTotal characteristics report shows several telltale signs of an encryption-based malware due to the DLL’s (Dynamic Link Library), requested permissions, and registry keys used by the application. The image below shows the files that were opened when the #Petya ransomware file was executed.
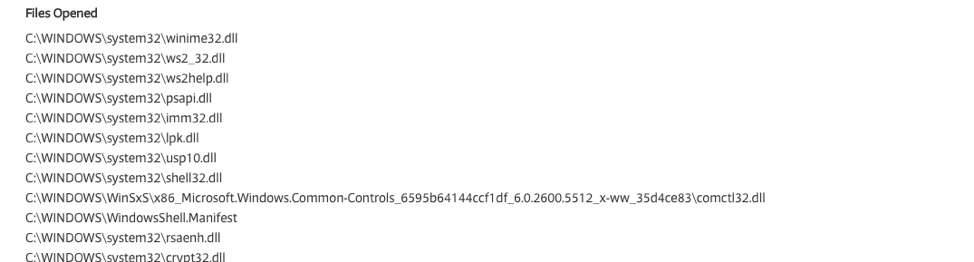
As you can see it interacts with crypt32.dll and rsaenh.dll, both of which are encryption libraries. The ransomware could be using these DLL’s for a few different things. The first use is decrypting itself. Typically, when ransomware is deployed it has to be deployed in such a way that it’s not easily detectable. From static analysis, we know that if a piece of software does A – B – then C, it’s likely ransomware, and this can be discovered before the application ever runs using sandboxes, md5 hashes, and reverse engineering. To get past this, attackers encrypt their malware to make it unreadable except for a small portion of the file called the “stub”. With the stub in place, and the application encrypted, the application’s execution is interrupted and forced to jump to the stub and run the instructions there first. When the stub executes, it steps through the application code and decrypts it. The image below shows a typical layout of an encrypted malware file.

But, with that said, none of the file interactions by themselves actually reveal any malicious activity. These files are used thousands of times a day by your computer.
Below are some additional characteristics discovered from the VirusTotal analysis. These characteristics are related directly to registry files.
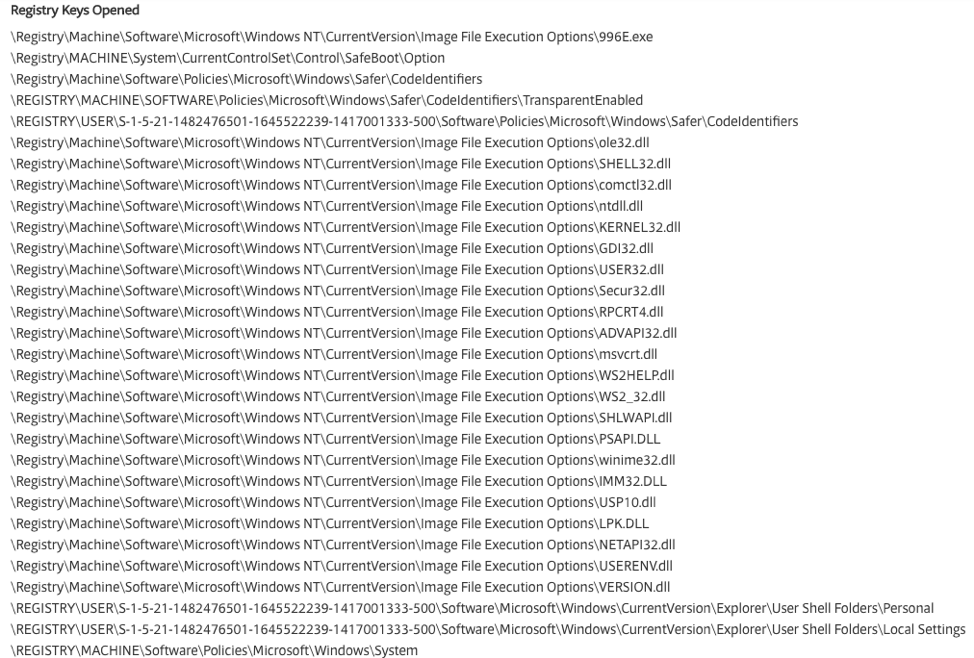
Please note, these registry keys are not a full list of keys affected but provide us enough context to achieve our goal of reviewing and understanding the ransomware characteristics. For a full list, please see the VirusTotal link in the sources section of this post.
A look at the registry keys above immediately raises several red flags. The very first registry interaction appears to be adding a PE (Portable Executable) “996E.exe” to IFEO (Image File Execution Options), which I’ve highlighted. IFEO is generally used for application debugging. Adding an application to IFEO allows a user, developer, or attacker to interrupt application execution. It can also be used as an execution point for malware, allowing an attacker to “attach” their malware to a legitimate application. The “996E.exe” application could be legitimate, since it has been in use by VPN and Bitcoin wallet applications in the past. The application is a well-known “packer”. A packer is used to compress multiple files into a single PE. Historically, packers have been used by malware to change the application signature and minimize the size of the application.
As we continue down the list, we can see the application is making modifications to SafeBoot settings. What does this mean? Well, in this case, it means that boot execution will be interrupted to display a ransom message. This particular strain of ransomware makes a modification to the MBR (Master Boot Record) preventing the user from booting into their operating system until the ransom is paid. Stepping further down the list, we can see that there are several more IFEO modifications made. Each of these DLL’s execution are modified allowing the ransomware to further control the underlying system.
So now that we see the registry modifications taking place, we have a good idea that this application is likely not a legitimate application, as most legitimate applications aren’t going to MiTM (Man-in-The-Middle) the execution of several system DLL’s, create a packer application registry entry, and change SafeBoot settings, but just to be sure we continue analysis of the application. The application requests permissions which tie directly to the MBR modification in the previous paragraph, “SE_SHUTDOWN_PRIVILEGE”. Why would the malware request permission to shut down the system? In this particular case, the malware has made modifications to the MBR, forcing it to boot to a “pre-boot” screen. An image of the common pre-boot screen can be seen below.
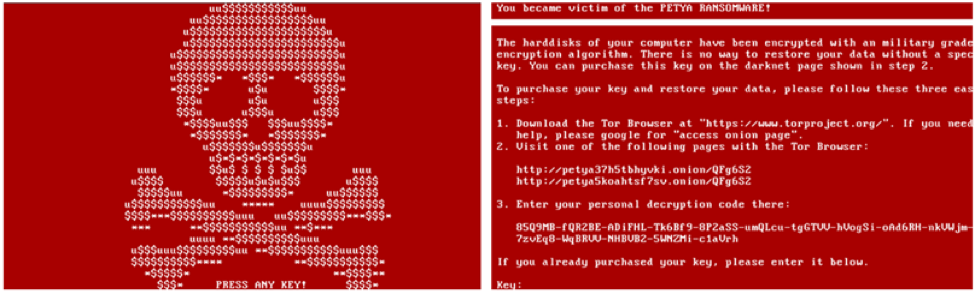
As we continue down the list, we can see the application is making modifications to SafeBoot settings. What does this mean? Well, in this case, it means that boot execution will be interrupted to display a ransom message. This particular strain of ransomware makes a modification to the MBR (Master Boot Record) preventing the user from booting into their operating system until the ransom is paid. Stepping further down the list, we can see that there are several more IFEO modifications made. Each of these DLL’s execution are modified allowing the ransomware to further control the underlying system.
So now that we see the registry modifications taking place, we have a good idea that this application is likely not a legitimate application, as most legitimate applications aren’t going to MiTM (Man-in-The-Middle) the execution of several system DLL’s, create a packer application registry entry, and change SafeBoot settings, but just to be sure we continue analysis of the application. The application requests permissions which tie directly to the MBR modification in the previous paragraph, “SE_SHUTDOWN_PRIVILEGE”. Why would the malware request permission to shut down the system? In this particular case, the malware has made modifications to the MBR, forcing it to boot to a “pre-boot” screen. An image of the common pre-boot screen can be seen below.
Ransomware can be very costly to remove, and sometimes can’t be removed without losing your data. Taking the proper steps and being proactive can ensure that you never have to go through the expensive and infamous ransomware experience.
Ransomware Propagation
Ransomware deployment happens in much the same way as any other malware. The major difference isn’t in the deployment or propagation, but in the underlying destruction of the malware itself. In 2017, a group of attackers took the then recently leaked MS17-010 (EternalBlue) exploit and paired it with a strain of ransomware. When the MS17-010 exploit was leaked, the world wasn’t prepared. It was an SMB exploit that compared to MS08-067, which most people never expected to see again. When the MS17-010 exploit was paired with a ransomware strain, it provided a small amount of logic: scan the network, fire the exploit, deploy the payload. This led to the malware spreading at an extremely fast rate. These strains came to be known as NotPetya and WannaCry.
While the NotPetya and WannaCry strains were the most popular at the time, they were not the only strains, nor was MS17-010 the only deployment method. Social engineering and exploit kits were just as common as MS17-010. An exploit kit contains several “exploits” which can be used to spread a piece of malware. These kits can be purchased from several “hacker” forums on the internet.
Defending Against Ransomware
Defending against ransomware and other adversarial threats can be a daunting task if not properly approached. Just like most malware, short of disconnecting from the internet and turning the system off, there is no perfect defense. However, there are several protections and precautions that can be used to reduce the risk of ransomware to almost nothing.
Data Protection
One of the best technical protections that can be implemented is proper backups. Implementing proper backups consists of (at a minimum) differential daily backups as well as weekly full disk imaging. The combinations of the two will ensure that infected systems can be rebuilt with a minimal loss of data. Even with a strong backup solution in place, it will be useless if the ransomware can access the backups, so ensuring that backups are properly segmented from the production environment is just as important as the backup itself.
Network Architecture
Prevention of ransomware, or even malware in general is a much more complex task than just implementing a backup plan. Proper defenses will be layered and segregated much like a grid on a chart. Network segments should be isolated and communication between business units should be kept at a minimum, and communications should pass through a managed and centralized logical location. In the event that ransomware breached your protected environment, it would be isolated to a specific business unit reducing the impact to the overall organization.
End User Awareness and Training
Properly layered protections go much further than network segregation, and proper network architecture. Increasing the awareness of end users is also considered a layer of defense, and arguably the most important layer. Showing users real-world examples of what a social engineering attack looks like will help them make better judgment calls on the emails they read or the files they open. Engaging with the end users and testing their awareness is also a great strategy to help understand where your weak users are, and to ensure that your end user training is effective.
Host-Based Security
Unfortunately, even with the most aware users and the best network architecture, it’s almost inevitable that some malware will get through your defenses and you will be one of two companies: one that spends a lot of time and money restoring from backups, or one who has additional layered protections.
When ransomware, or any malware makes it through your entire suite of protections, your last line of defense is the host-based security. In a perfect world your organization will catch the ransomware before it ever makes it this far and host-based protections would act more as a redundancy, but this is not the case.
Applying a strong host-based security system to your endpoint can save loads of time and money that would otherwise be spent removing nuisant viruses and spyware. But even better than that, selecting the correct endpoint solution can do much more. Some endpoint solutions have the ability to breakdown the characteristics of applications ran on a system in real-time and determine the risk of the application, much like we did in the previous section of this blog. If the application was determined to be malicious, the administrator has the ability to quickly react and isolate or remove the threat.
Centralized Management
Even with all of the top of the line hardware and software protections, if it’s unmanageable, it will be forgotten until a breach happens. Building a manageable centralized solution is just as important as every other layer of the protection. At this point all of your existing solutions play some role in protecting your environment. All of which will provide some alerting or logging system. Bringing this data together and correlating it against events happening on your network is an important part of your data protection. Without a centralized and manageable console, your analysts will become overwhelmed and threats will be missed.
A SIEM will bring together multiple data points from all of your security or technology solutions with the ability to flag certain characteristics which look suspicious. Having a properly configured SIEM and a well-trained security team, or a third-party managed security service partner can assist in capturing the otherwise invisible network and application threats.
In conclusion…
Ransomware, like other malware, has many different strains, each of which can present different levels of risk. If you’re reading this because you’ve been caught off-guard by ransomware, it’s likely too late, but there is some hope. Doing research on the strain of ransomware can sometimes result in tools or keys that can be used to decrypt the ransomware. In worst case scenarios, I’ve seen several people pay the ransom to recover their files, but this is still not guaranteed and should generally be avoided if possible. If you’re here because you’re taking proactive measures to protect your data, then you’ve already accomplished the hardest part, just remember to layer your defenses and isolate the threat.
Sources:
https://www.symantec.com/content/dam/symantec/docs/reports/istr-23-2018-en.pdf

